Forget fancy algorithms and zero-day exploits. Cybercriminals’ most powerful weapon is not a line of code, but the person reading this, with their hopes, fears, and trusting nature. Social engineering involves hackers exploiting the human mind to bypass firewalls and steal data, posing a significant threat to the security of our digital systems.
Understanding social engineering is crucial for staying safe in the digital jungle, as it provides a foundation for understanding and preventing potential threats. Imagine receiving an urgent email from your bank, a friendly call from IT support, or a convincing pop-up requesting immediate action. Some tactics are employed to deceive unsuspecting victims into compromising their own security.
But why do cyber attackers commonly use social engineering attacks? The reason for exploiting human psychology when there are technical vulnerabilities is because people are often the weakest link. Hackers exploit our vulnerabilities, exploiting fear, greed, and a desire to help others, to create sophisticated schemes that exploit our emotions and hinder critical thinking.
This blog post delves into the intricacies of social engineering attacks, revealing common cybercriminal tactics, and equipping readers with the necessary knowledge and tools to protect against these threats.
-
Bypassing the Technical Fortress
Cybersecurity measures frequently focus on technical safety measures, such as firewalls and software patches. However, social engineering exploits human nature by bypassing these protections. Phishing emails, fake tech support calls, and creative social media postings can deceive even the most careful user into revealing important information or installing malware.
-
Using Trust and Emotions
Humans are friendly, trustworthy, and empathetic. Attackers utilize these characteristics by creating fear, urgency, or curiosity. Attackers use our emotional weaknesses in many ways, such as a panicked phone call saying your bank account has been hacked, an apparently real email offering a free gift card, or a malware download that looks like a harmless update.
-
Tailoring the Attack
Social engineering attacks are more tailored than brute-force hacking. Attackers research targets’ internet behavior, interests, and social connections. This lets them create messages and circumstances that resonate with the person, making them more manipulable.
-
The Cost-Effective Option
Resources are needed to develop and deploy complicated malware. Social engineering, however, requires little technical knowledge and resources. As a result, cybercriminals of all kinds find it very appealing, which helps explain why it is so common.
-
The Changing Landscape
As social engineering approaches gain recognition, attackers adapt and develop. They reinvent methods, use social media, and improve psychological manipulation. The game changes constantly, so you must stay alert and educated.
Frequently Asked Questions (FAQ’s)
Why do people fall for social engineering attacks?

Humans are built for trust and empathy. Phishing, pretexting, and baiting use these inherent impulses to create urgency, fear, or duty, bypassing critical thinking. Personalized storylines that evoke emotions make us more manipulable.
Why hackers normally engage social engineering in most of their activities?
It’s all about efficiency and effectiveness. Social engineering is:
- Faster and cheaper: No need for costly hacking tools or complicated coding.
- More successful: Social ploys are more effective than technological attacks.
- Wider reach: Targets anyone, regardless of technical expertise.
Who do cyber attackers commonly use social engineering attacks on?
Everyone! If someone has valuable information or access, they could be the target of a targeted attack. These attacks are usually aimed at leaders or well-known people. Hackers may target age, career, or online behavior vulnerabilities.
How do attackers use social engineering?
They use many methods, including:
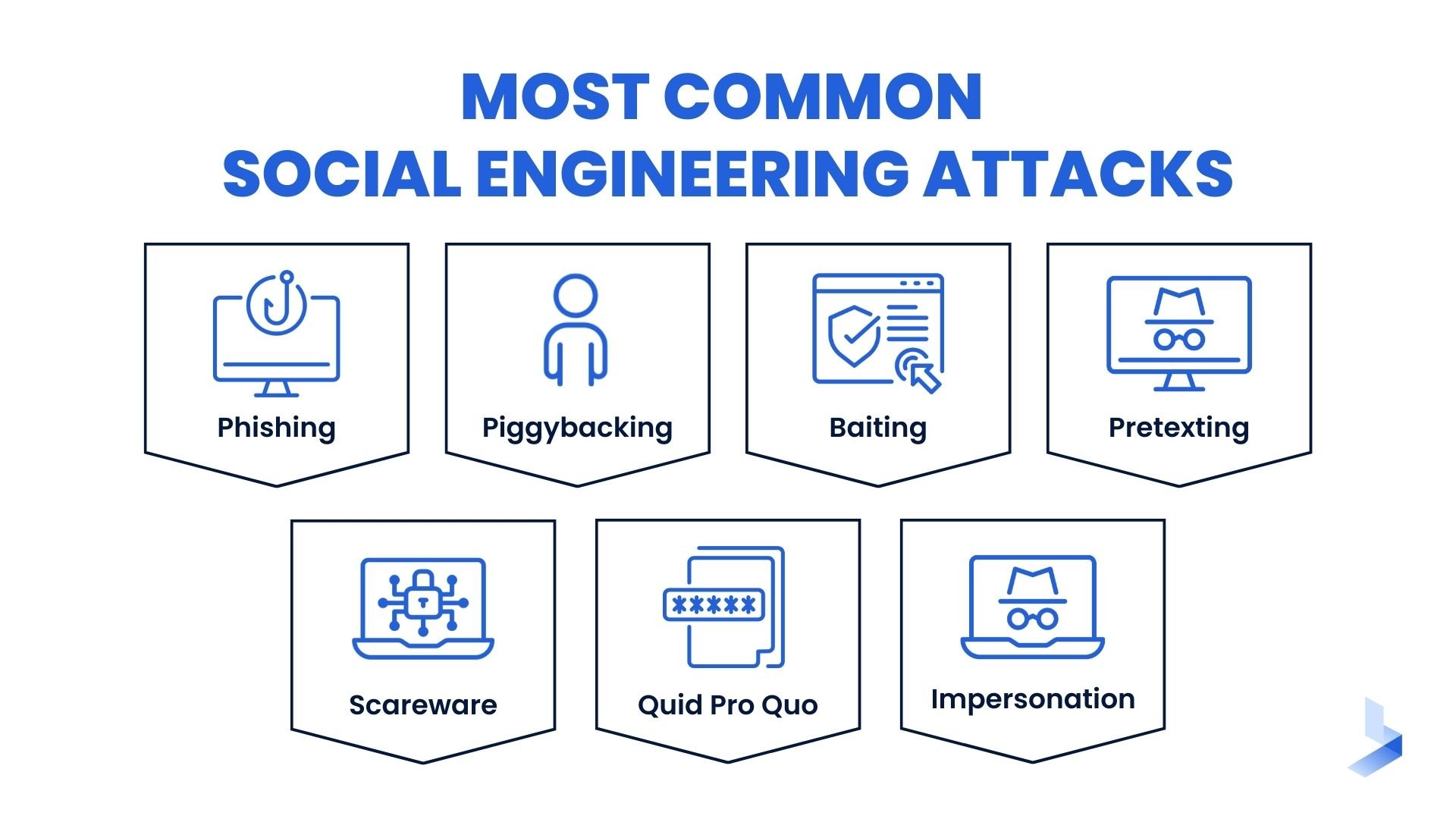
- Phishing: Emails, texts, and social media messages trick victims into sharing information or clicking links.
- Pretending to be tech support to win trust and access systems or data.
- Baiting: Offer tempting bargains or malware-laden freebies.
- Spear phishing: Sensitive information is used to send targeted threats to specific people.
- Quid pro quo: Trading something worthwhile for knowledge.
How common are social engineering attacks?
Extremely common! Phishing attacks alone reach millions daily, making them one of the biggest cyber risks. Cybercriminals like them because they’re easy to use and effective.
What is a common method used in social engineering?
Phishing is still the most common way because it works so well. Hackers send emails or texts in the name of banks, authorities, or friends to get victims to click harmful links or expose important information.
Why is it called social engineering?
The word refers to manipulating human behavior and social dynamics for a specific goal. Just like engineers use tools and knowledge to build structures, social engineers utilize deception and psychology to “build” their plans and exploit human vulnerabilities.
Why are social engineering attacks difficult to prevent?
They use our natural trust and feelings against us, which makes it harder to spot them. Also, it’s hard to stay ahead of the curve because methods and personalization are always changing. However, being informed, being skeptical, and practicing good cybersecurity practices can make the chance of falling victim far less likely.
Social engineering is complex, but knowing it can help us traverse the internet safely. Remember that you are the gatekeeper to your digital world—stay knowledgeable, vigilant, and ahead of hackers.
The next time you see a tempting email link, a “free” file that sounds too good to be true, or a tech support call in a panic, remember this: you have the power to defuse the bomb. Your knowledge, your awareness, and your doubts are the best defenses you can have against social engineering.
Leave a Reply