Let’s say you’re checking your email and a message comes from someone you know and trust. The email seems important and needs your quick attention. Clicking your mouse just once may have fooled you into a spearphishing attack, putting your private information and personal data at risk.
Spearphishing emails look like they are from a trustworthy source, but they really are not. They look like they are real, and they often use personal information and well-known names to get you to trust them and take advantage of your weaknesses. Even for people who are very good with technology, these complex scams can take time to spot.
So, what helps protect from spearphishing in this digital world? There are strong ways to protect yourself from spearphishing threats that you will learn in this blog post.
We’ll talk about the tricks these cybercriminals use to get what they want, teach you how to spot and avoid their traps, and give you the confidence to protect your data and privacy.
How Spear Phishing Works?
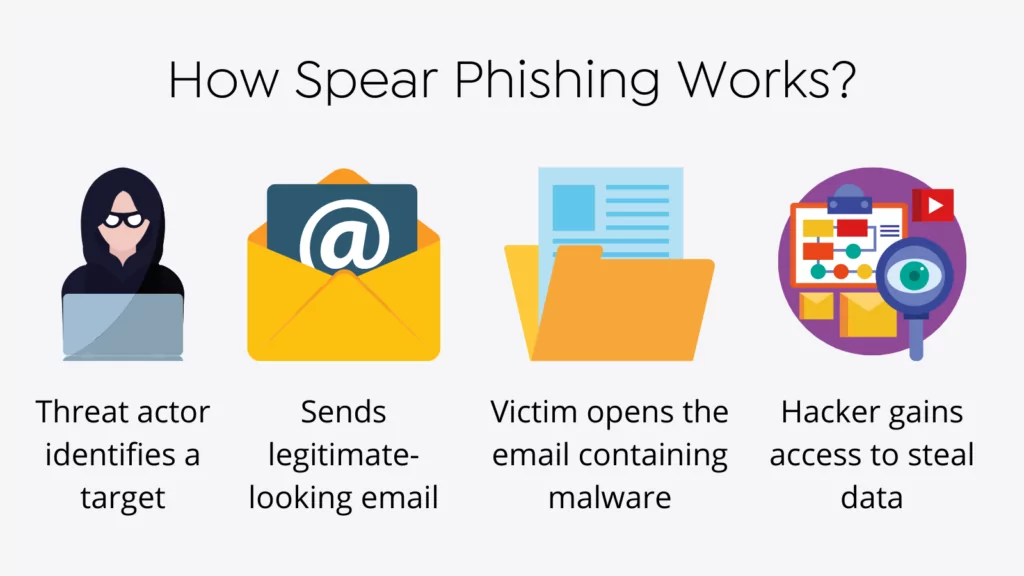
Spearphishing scams typically consist of three steps:
Target Acquisition and Research:
The attacker figures out which person or group could be a target. One of these people could be a company boss or someone with access to private data. They get information about the target, like their name, job title, company, coworkers, hobbies, and anything else that can help them make the phishing email more personal.
Crafting the bait:
The attacker uses the information they’ve gathered to make a personalized email that looks like it came from a trusted source, like a coworker, a bank, or a service provider.
The Deceptive Trap:
The email is meant to make the target feel rushed or trustworthy, and it often includes private information about the target to make it seem even more real. The email usually has a call to action that tells the receiver to reveal private information, click on a harmful link, or download a fake document.
When the target clicks on the harmful link, it takes them to a fake website that perfectly mimics the real website of the apparent sender.
On the other hand, the link could download malware onto the victim’s computer, letting the attacker steal private data or log into the victim’s accounts without permission.
If the victim types their login information or other private details on the fake website, the attacker can get this information immediately and use it for bad things.
Why Spear Phishing is Dangerous?

Spearphishing can ruin companies as well as people. Victims may also experience:
- Identity theft: Hackers can start accounts, incur debt, and ruin your credit score using stolen information.
- Financial loss: Cybercriminals might steal money from your bank accounts using stolen information.
- Business damage: Spear phishing attacks can breach important business data, disrupt operations, and destroy reputations.
Protecting Yourself from Spear Phishing
You can stay safe from spearphishing attempts in several ways, including:
- Educate yourself: Find out the most common tricks phishers use and how to spot emails that look phishing.
- Be careful: Do not open links or files in emails from people you don’t know or trust.
- Verify senders: Always check the sender’s email address and website name to ensure they are correct.
- Hover over links: Move your mouse over links: Before you click on a link, move your mouse over it to see its URL.
- Make your passwords strong: For each of your online accounts, make sure the password is strong, and don’t use the same password for more than one.
- Two-factor authentication enhances the security of your online accounts by adding a second verification factor, such as a code sent to your phone.
- Keep your software up-to-date. Keep your computer’s operating system, web browser, and other apps up-to-date to protect against known security holes.
- Seek help. If you get a strange email, tell the sender’s email provider and your IT staff about it.
What are anti-phishing tools?
Anti-phishing tools are software applications that detect and prevent phishing attacks by analyzing emails using various techniques.
- Content analysis examines phishing emails’ words, sentences, and grammatical patterns.
- URL analysis involves checking the email’s links against lists of known scam websites.
- Sender verification ensures the authenticity and authorization of the sender to send the message.
- Attachment analysis: looking through files for harmful code or threats that are hidden inside them.
These tools offer a comprehensive defense against phishing attacks and can function independently or be integrated with existing email security solutions.
Can antivirus detect phishing?
Traditional antivirus software can identify phishing attempts, but not always. They focus on discovering and eradicating known malware and viruses, while phishing attacks exploit human vulnerabilities through social engineering.
To protect against spear phishing, organizations need antivirus software, cyber awareness training, strong passwords, two-factor authentication, and dedicated anti-phishing technologies.
These tactics and online security precautions will significantly lower your risk of spearphishing attacks and secure sensitive data. Vigilance is essential in the ever-changing digital world.
It’s essential to protect your digital life from cyberattacks, especially spearphishing. You may confidently protect your sensitive data and explore the internet with the knowledge and tools in this guide.
Cybersecurity is a continual process. Stay alert and aware, and upgrade your defenses to combat evolving threats.
Leave a Reply