Have you ever gotten an email or received a phone call that felt too good to be true? Scammers may have lured you with a contest to win a free vacation or a warning about your hijacked bank account. If so, you have been the victim of social engineering, a cunning tactic scammers use to trick people into disclosing personal information or engaging in other potentially harmful behaviors.
In this blog post, we’ll look at social engineering and the tactics scammers employ to manipulate individuals. We’ll also provide you with practical advice on how to avoid falling victim to these deceitful scams. So buckle up and prepare to discover how can you protect yourself from social engineering and avoid becoming a victim of social engineering scams.
Understanding the concept of social engineering

The art of using human psychology to acquire access to information, systems, or assets is known as social engineering. Scammers use a number of strategies to deceive their victims, frequently depending on emotions like fear, urgency, or greed. Common strategies include:
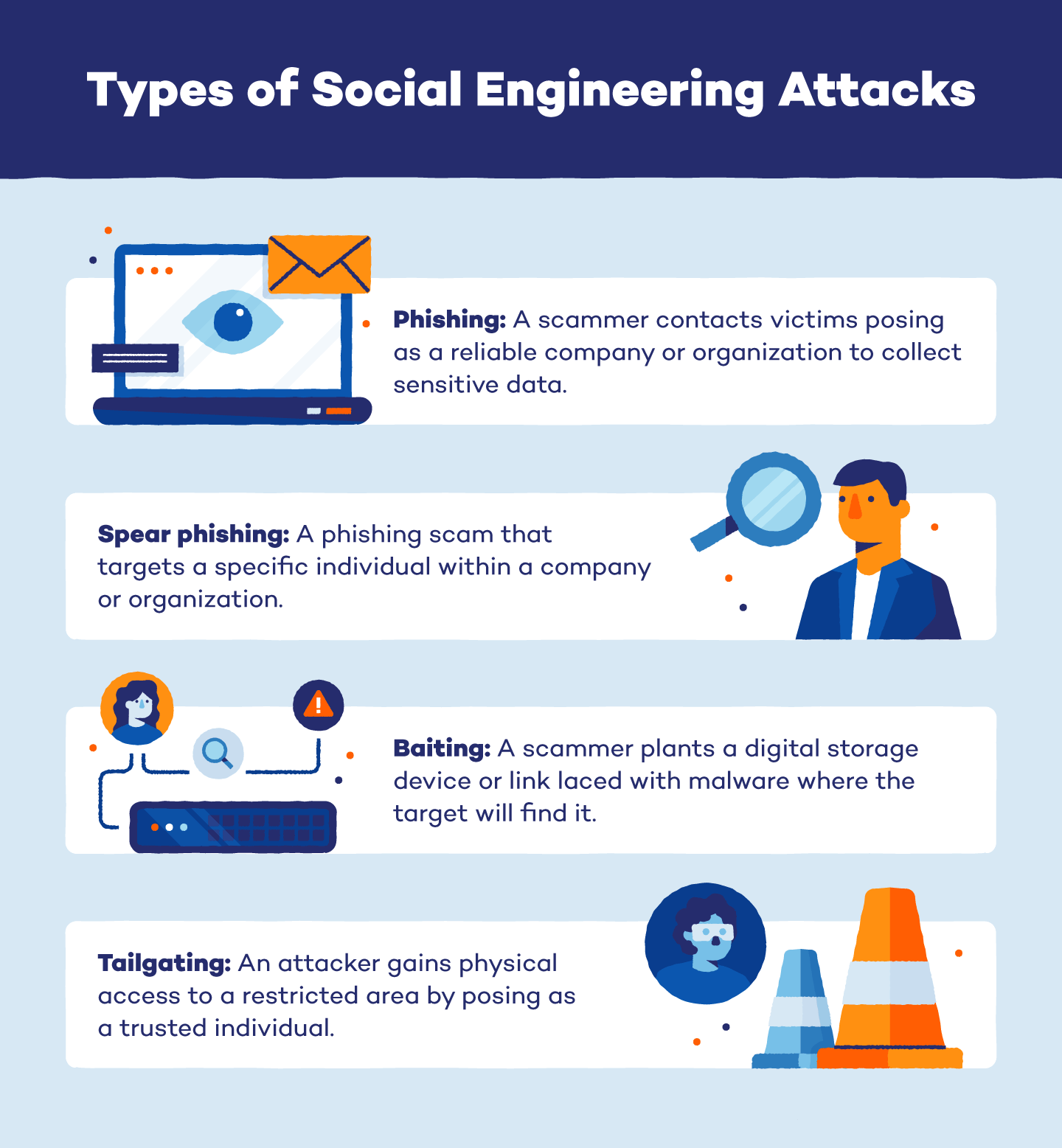
- Phishing: Phishing is the practice of sending emails or text messages that appear to be from reputable sources, such as banks or social media platforms, in order to dupe recipients into disclosing personal information or clicking on dangerous links.
- Pretexting: Assuming a false identity, such as a customer service representative or a technical expert, in order to acquire the target’s trust and obtain sensitive information.
- Baiting: is the practice of enticing people to give personal information or download malware by providing something appealing, such as a free gift or prize.
The Impact of Social Engineering
Falling victim to social engineering can have serious implications, ranging from financial losses and identity theft to reputational damage and even physical violence. The average cost of a data breach in the United States will be $9.48 million, indicating the tremendous financial impact of such attacks.
Protecting yourself from social engineering

While social engineering attacks are becoming more complex, there are several practical measures you may use to protect yourself:
- Be skeptical: Never take an email, phone call, or text message at face value. Always confirm the sender’s legitimacy by contacting the organization directly via their official website or phone number.
- Avoid Link Clicking: When clicking on links in unsolicited emails or messages, proceed with caution. Before clicking, hover your mouse over the link to see the exact URL. If it does not correspond to the desired destination, do not click it.
- Protect Personal Information: Never send sensitive information over email or text message, such as passwords, credit card numbers, or social security numbers. Legitimate organizations will never request this information in these ways.
- Be Wary of Urgent Requests: Scammers frequently instill a sense of urgency in their victims in order to drive them into responding rashly. If you are under pressure to act immediately, be careful and take your time to check the request.
- Educate yourself: Keep up-to-date on the newest social engineering strategies and trends. Read security blogs, newsletters, and advisories to stay up-to-date on emerging dangers.
Additional Tips for Enhanced Protection:
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security to your online accounts makes illegal access much more difficult.
- Install Anti-Malware Software: To detect and block harmful software, keep your devices secured with up-to-date anti-malware software.
- Be Mindful of Social Media: Avoid posting personal information or connecting with dubious personas on social media networks.
What is the Best Way to Protect Against Social Engineering?
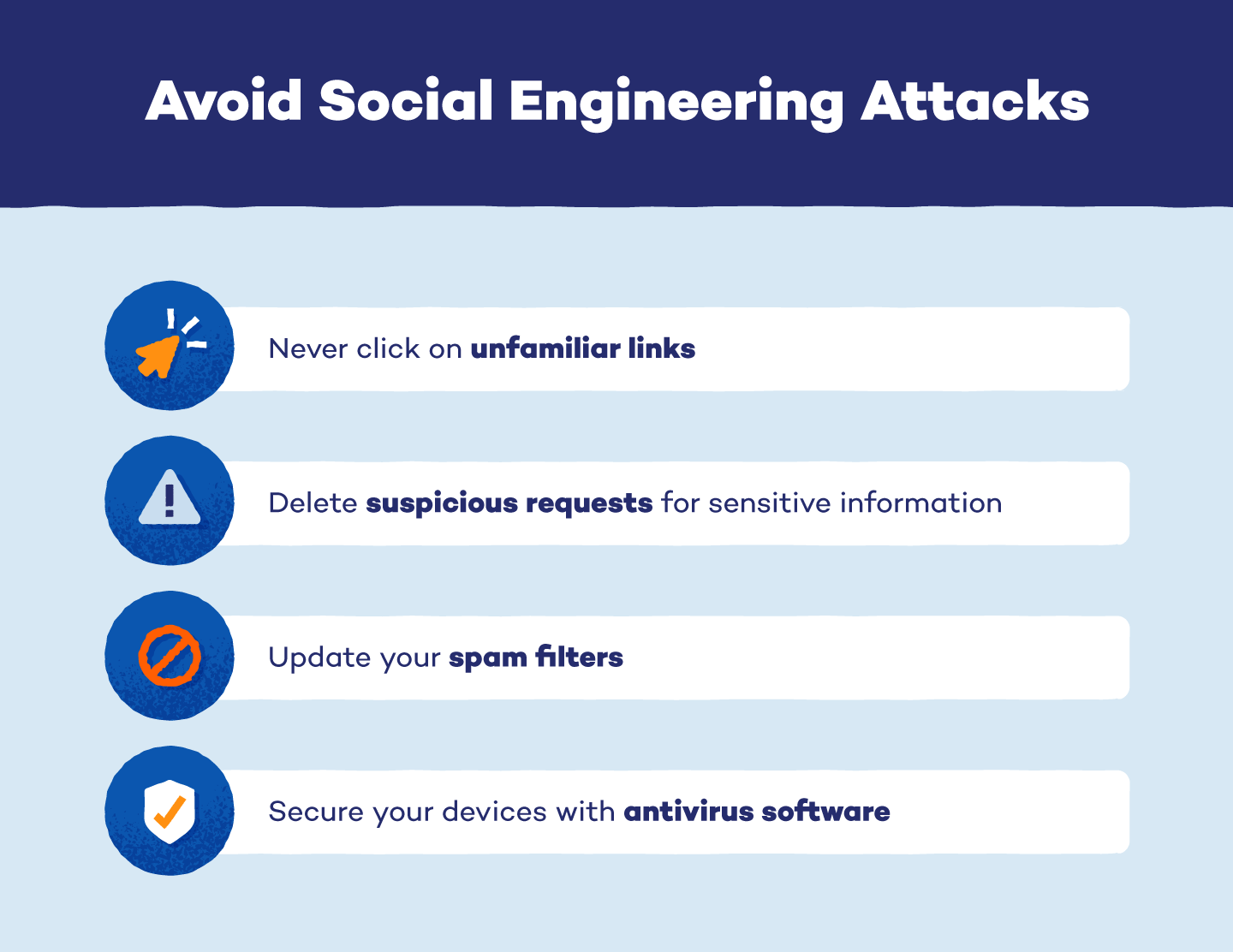
The easiest method to protect oneself from social engineering attacks is to be aware of common scammer strategies and to put strong countermeasures in place. Here are a few points:
- Avoid unauthorized emails, phone calls, or text communications.
- Never send personal information by email or text message, such as passwords or credit card numbers.
- Hover your mouse over links in emails or messages to see the full URL before clicking.
- Exercise caution when faced with urgent demands or offers that seem excessively advantageous.
- Install and keep anti-malware software up-to-date.
- Make two-factor authentication (2FA) available for your online accounts.
Why are social engineering attacks difficult to prevent?
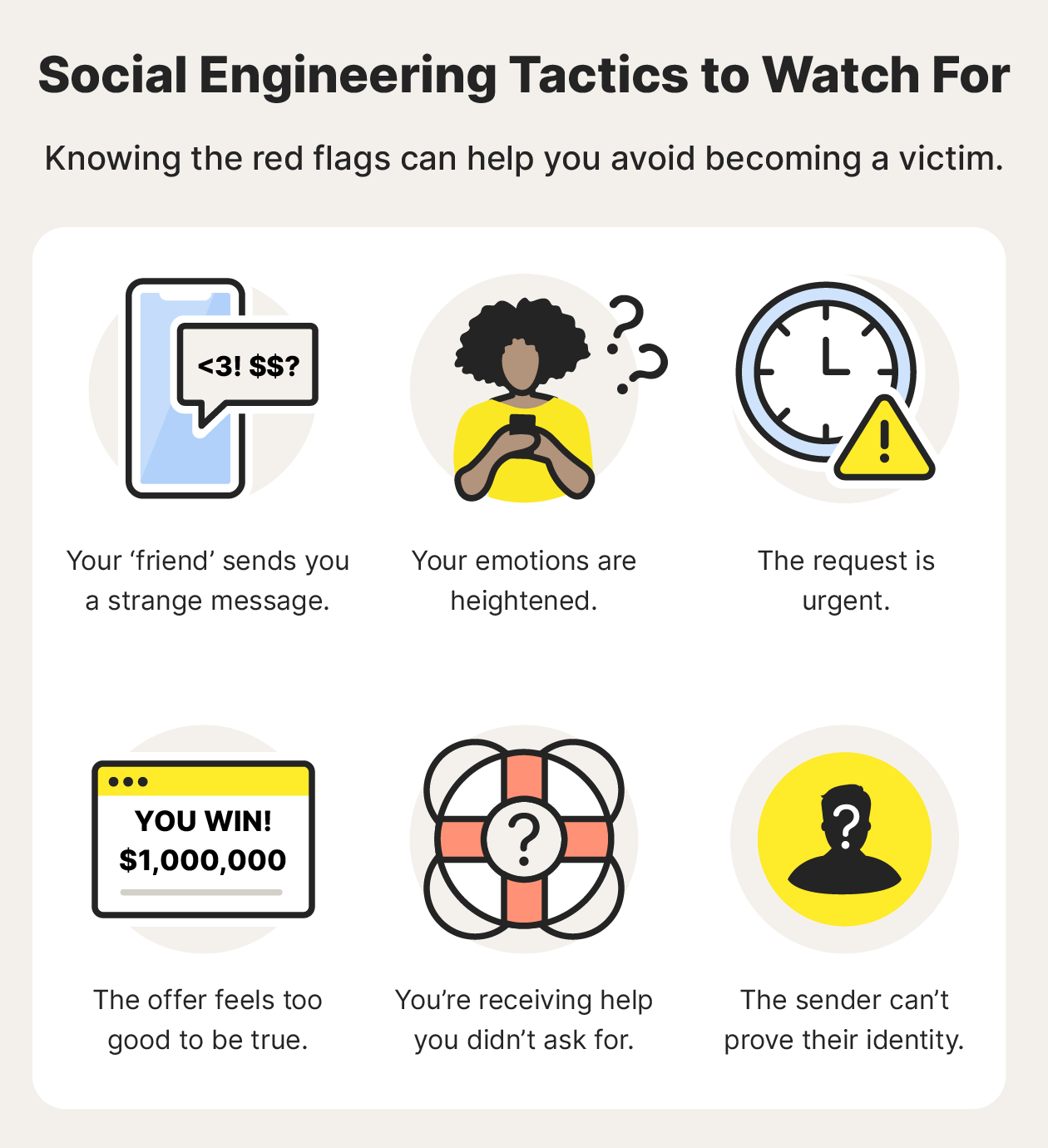
Social engineering attacks are difficult to prevent because they exploit human vulnerabilities and emotions. Scammers frequently instill a sense of urgency or anxiety in their victims in order to drive them into behaving rashly and without thinking properly.
How Can You Protect Yourself from Social Networking Sites?
Follow these steps to protect yourself from social engineering assaults on social networking sites:
- Limit what kind of personal information you post on social media.
- Be aware of strangers making friend requests.
- Do not open attachments or click on links from unknown senders.
- Share your location or travel plans with caution.
- Control who can view your posts and information by adjusting your privacy settings.
How can social engineering happen in person?
Scammers may exploit physical appearance, authority, or familiarity to earn the trust of their targets during social engineering. In-person social engineering strategies include the following:
- To obtain entrance to a home or office, impersonate a repair worker or service technician.
- To collect confidential information, pose as a coworker or friend.
- Tailgating someone into a restricted location without permission
How can social engineering be a threat?
Social engineering is a serious risk to people and companies, and it can have the following effects:
- Financial losses: Scammers may entice victims to provide credit card numbers or bank account information, allowing them to steal money or carry out fraudulent activities.
- Identity thieves can steal personal data such as passports, driver’s licenses, and social security numbers through social engineering attacks and exploit it for identity fraud.
- Reputational harm: Through bad press, a decline in trust, and potentially legal implications, social engineering can harm a person’s or an organization’s reputation.
- Social engineering attacks that break an organization’s security measures may expose sensitive customer or employee information, leading to data breaches.
Which Best Practice Can Help Defend Against Social Engineering Attacks?
A mix of awareness, doubts, and awareness is the most effective strategy to protect against social engineering attempts. Educating yourself on social engineering techniques, being wary of unwanted contacts, and implementing solid cybersecurity measures will dramatically lower your chances of falling victim to these scams.
What are social engineering examples?
Here are some examples of common social engineering attacks:
- Phishing emails: It looks to be from reputable sources, such as banks or online stores, and frequently contains links that, when clicked, redirect to dangerous websites that may collect personal information or install malware.
- Tech support scams: Scammers may contact or email people acting as tech support staff from well-known companies in order to acquire remote access to their computers or devices in order to install malware or steal personal information.
- Fake invoices: Scammers may send fake invoices or bills that look to be from reputable merchants, duping individuals or organizations into paying bogus charges.
- Social media scams: Scammers may build phony profiles or hijack legitimate accounts on social media to convey misinformation, solicit personal information, or promote fraudulent schemes.
Why is social engineering effective?
Social engineering attacks are frequently successful because they take advantage of human psychology and rely on our natural instincts to trust others, assist others, and avoid conflict. Scammers meticulously tailor their words and strategies to elicit emotions such as fear, anxiety, or greed, allowing them to manipulate their targets into completing desired behaviors.
How common is social engineering?
In the modern digital age, social engineering is a common threat. A recent Ponemon Institute survey found that social engineering attacks affected 83% of firms in the last year. The cost of these attacks can be significant, with the average data breach in these countries are massive.
What is social engineering in today’s society?
In today’s world, social engineering has become more sophisticated as scammers alter their strategies to take advantage of the latest technologies and trends. Individuals and companies are continually vulnerable to potential social engineering assaults as their reliance on social media, mobile devices, and cloud-based services grows.
What is the most commonly used social engineering technique?
According to a recent report by the Anti-Phishing Working Group, phishing emails continue to be the most common kind of social engineering attack, accounting for more than 80% of reported incidents. Scammers frequently use phishing emails to deceive users into disclosing sensitive information such as passwords, credit card details, or social security numbers.
What is the most successful form of social engineering?
The success rate of social engineering attacks varies according to the technique used and the target’s level of awareness. Phishing emails, on the other hand, remain one of the most effective forms of social engineering, with an estimated open rate of 20% and a click-through rate of 2%.
Individuals and organizations are both vulnerable to social engineering. Understanding scammers’ strategies and executing effective countermeasures will dramatically lower your chances of falling victim to these deceitful scams.
Remember that social engineering is more than simply technology; it is also about understanding human behavior. You may empower yourself to make informed decisions and defend yourself from these damaging attacks by learning about scammers’ strategies.
Learn more about social engineering to take the first step in ensuring your online security. Visit our website for a complete guide to preventing social engineering, including tips, tools, and best practices.
Leave a Reply