Have you ever been tempted to click on a link or disclose sensitive information after receiving an email from a reputable institution? Hackers use phishing as a method to access accounts and steal personal data.
What does phishing mean?
Phishing, a form of “fishing,” involves the distribution of fake emails or messages to deceive individuals into providing personal information. Emails often adopt the tone and style of renowned brands, including logos and terminology, to enhance their official appearance.
This article delves into various forms of phishing, its psychology, and effective strategies to protect your online identity and personal information.
Phishing: What Is It?

Phishing is a deceptive method that involves sending electronic messages or emails claiming to be from reputable sources like banks, credit card firms, or government authorities. Misleading communications aim to deceive individuals into providing personal information or visiting phishing websites, thereby exposing them to malware infection.
The Anatomy of a Phishing Attack
There is a common pattern that phishing attacks usually follow:
The Bait: Cybercriminals craft emails or messages that look to be from a trusted source, frequently employing recognizable logos, branding, and language to engender trust.
The Hook: Typically, the communication involves an urgent request or warning, pushing the recipient to take rapid action. The sense of urgency distorts judgment and encourages rash decisions.
The Catch: The communication frequently includes a link or attachment that, when clicked or opened, causes the cybercriminal’s desired effect. This could include malware installation, redirection to a phishing website, or direct disclosure of sensitive information.
The Psychology Behind Phishing’s Success
Cybercriminals exploit our cognitive processes and vulnerabilities to deceive us into falling for phishing scams. A master of social engineering, they appeal to our emotions rather than our reason.

- Fear of Loss: Phishing messages frequently use our fear of financial loss or identity theft, instilling a sense of urgency in us to comply with the attacker’s demands.
- Sense of Authority: Cybercriminals may imitate trusted authority figures, such as bank personnel or government officials, taking advantage of our natural tendency to obey and trust authority.
- Curiosity: Phishing emails may spark our interest, luring us to click on links or open attachments without thinking.
The Evolving Landscape of Phishing
Cybercriminals use new methods as technology progresses. Advanced phishing attacks target unwary victims by bypassing security.
- Spear phishing: This targeted form of phishing uses personal information to send highly tailored, deceptive messages.
- Whaling: Cybercriminals target CEOs and executives who may have access to valuable company data or financial information.
- Smishing: SMS phishing attacks, typically imitating bank or delivery service messages, are becoming more common.
Protecting Yourself from Phishing Attacks
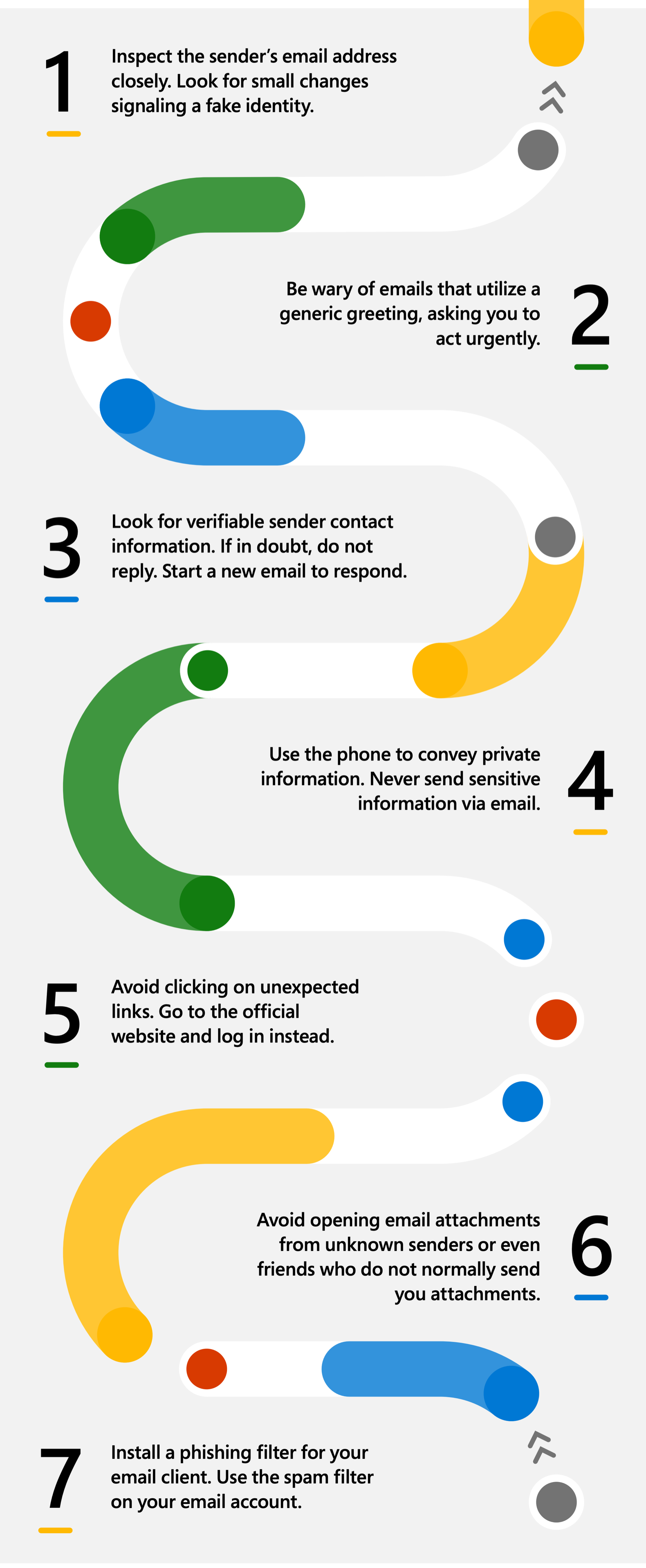
Phishing attacks can be complex, but awareness is your first protection. Here are some important safety measures:
- Check emails and texts: Be cautious of unwanted emails or texts urging immediate action. Contact the organization through a trustworthy source to verify the sender’s identity.
- Hover over Links: Before clicking, hover over links to see their destination URL. Avoid clicking on URLs that don’t match website addresses.
- Avoid Attachments: Do not open unknown attachments. Use a trusted antivirus or anti-malware tool to scan attachments for viruses.
- Allow 2-Factor Authentication: Enable two-factor authentication to secure your accounts beyond your password.
- Stay informed: Share the latest phishing strategies with friends, family, and coworkers.
Frequently Asked Questions (FAQ’s)
What’s a phishing example?
Phishing is a fraudulent practice that involves deceiving individuals into disclosing sensitive information or engaging in activities that could potentially harm them or their businesses. Phishing scams often involve posing as emails, texts, or social media posts from banks, credit card firms, or government authorities.
Phishing email example:
Urgent action is needed. Account Verification
Respected Client,
We found suspicious behavior on your account and need your quick attention to verify your identity and prevent unauthorized access.
Click the link below to validate your account:
Website for phishing
Sincerely,
[Bank or institution name]
What is meant by a phishing attack?
Phishing attacks use fake emails, texts, and social media posts to steal passwords, credit card data, and Social Security numbers.
What is a famous example of phishing?
Famous phishing attempts have occurred throughout history. Some of the most notable:
AOHell (2003): One of the first and most significant phishing attacks. Attackers tricked AOL users into clicking on a link to verify their details by sending them fake customer support emails indicating a hijacked account. The link took users to a bogus AOL page where attackers grabbed their credentials.
Nordea Bank Incident (2007): An attack on Swedish bank Nordea Bank clients occurred in 2007. Attackers sent fake security emails to Nordea clients, notifying them of suspicious activity and requesting them to update their information via a link. The link led to a phony Nordea Bank website, where attackers collected user credentials.
Operation Phish Phry (2011): targeted RSA security workers. The attackers sent RSA employees fake emails from colleagues. The emails’ attachments planted a Trojan horse on employees’ PCs. They broke into RSA’s network using employees’ credentials stolen by the Trojan horse.
Phishing emails targeted Epsilon, a data processing provider, and exposed the login information of over 60 million consumers of TJ Maxx, Marshalls, and Barnes & Noble in 2011.
Dyre Phishing Scam (2013-2015): The 2013-2015 Dyre Phishing Scam targeted organizations with sophisticated phishing attacks, using social engineering to gain employees’ trust, steal login credentials, and bank account numbers. Business losses from the Dyre phishing scheme exceeded $100 million.
Facebook and Google BEC Attack (2017): A BEC attack on Facebook and Google in 2017 resulted in employees receiving fake vendor emails from the attackers. Emails instructed staff to transfer funds to vendors’ bank accounts. The employees sent over $100 million to the attackers’ accounts without realizing the vendors were bogus.
Is phishing spam?
Phishing emails are not spam, despite containing unsolicited communications and false material, as spam is mass-produced, generic, and generally marketable. Phishing emails deceive individuals into disclosing personal information or engaging in harmful activities.
Is phishing an example of a virus?
Phishing deceives individuals into providing information or acting, unlike malware or viruses, which disrupt computer systems.
Phishing, a growing threat in the digital world, traps unsuspecting victims. By understanding the psychology behind these attacks and taking precautions, we can greatly reduce our likelihood of falling victim to them.
Knowledge and diligence are crucial in defending against cybercriminals’ manipulation. Stay updated on the latest phishing tactics and share your knowledge. To safeguard your digital identity, sensitive data, and online confidence, use strong passwords, multi-factor authentication, and avoid unsolicited emails, texts, and calls.
Gain knowledge and tools to navigate the digital world safely and protect your digital identity by understanding phishing.
Leave a Reply